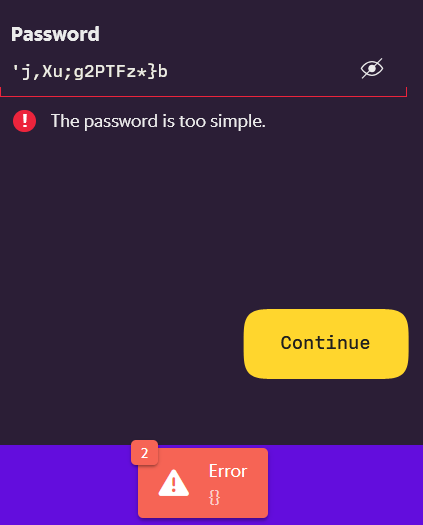
I hate these arbitrary limitations of 16 characters, 25 is unbreakable and some sites won’t slow it.
You might want to try out: https://libraryofbabel.info/random.cgi
“for best results, your password should be the street you grew up on or your favourite book”
It says NO special characters!

64 characters picked at random in
[]is perfectly fine if password is your only option. Special character do not increase significantly the difficulty of bruteforcing it, but introduce the risk of having to manually type"}à.å÷Â!!ç-×ô@¸Á¢±ãÕß>>úÓ}¼º¤«<_`àÅû§Æ]*ÂñçÌÿ§à®&ܱ=Ú-´ð¹é$.>=;Öif something goes catastrophically wrong.Not being allowed to use special characters can be a sign of the website saving your password in plain text.
Yes because if you choose 8 characters at random, with 25 small + 25 big letters and 10 numeric, it* only 60^8 = 167,961,600,000,000 combinations.
I think the problem is more if the system allow brute force with thousands of erroneous attempts.
I never got the frantic entropy mindset, when the problem is much simpler to not allow endless attempts. You can allow 50 attempts, and chances would be very slim to guess even pretty moronic passwords.what’s an example of password that can be guessed by logic?
Something that can possibly be deduced knowing personal information, like a birth date.
hunter2
Most websites don’t allow multiple failed logins and, even if they did, the network latency alone would make brute force attacks useless. The point of having a high entropy password is to protect against hackers brute forcing a leaked database of hashes. Having different passwords for every website also protects against this so, as usual, the answer is “just use a password manager”.
The point of having a high entropy password is to protect against hackers brute forcing a leaked database of hashes.
I don’t think you need to worry about that in this case, the special character restriction suggests to me that they don’t hash it.
The point of having a high entropy password is to protect against hackers brute forcing a leaked database of hashes.
Seems a bit stupid if a database of passwords or other sensitive information can be brute forced.
Please clarify what you mean because your comment is giving me these vibes.
just use a password manager
I will never do that, I have a system instead. I never understood why people would want to use a password manager. To me it seems it ads an attack vector, where you could lose EVERYTHING!
Passwords suck as an authentication system in general. Your own system is probably worse than what password managers do. Yes, there are problems, but so does every other solution to this, and password managers win out in the comparison.
Your own system is probably worse than what password managers do.
How so? If you use a password manager across 3 platforms, that makes for 3 attack vectors.
My personal system has guaranteed no vulnerabilities. So how do you conclude my system is worse?My personal system has guaranteed no vulnerabilities
If you think that’s true, then you don’t have the experience to make a secure system.
What? What kind of system do you think I have? The only vulnerability is if they can hack my brain.
Yeah, that’s going to be a terrible system. The human brain isn’t capable of keeping track of enough entropy to create a secure password system.
More generally, it’s a big red flag when anybody thinks they can make a better system than publicly available and verified systems. You’re not capable of that, I’m not capable of that, Bruce Schneier is not capable of that. No matter how smart you are, you missed something. That’s why I didn’t need to know a single detail.
I guarantee your system is less secure than the worst password manager. Humans are inherently bad at choosing passwords, or anything to do with randomness really.
Use a password manager
I mean, 63^6 is a lot of possibilities, but just make the password longer to increase its security.
Blocking out special characters is dumb, but as others have pointed out, they’re probably not sanitizing inputs.
At least if you ever forget it, they’ll be able to email it to you.
Try this one, has lots of special characters:
a_a_a_a_a_a_a_aThis one too: _____________
Lol I recently have found the opposite!
Fandom is gross anyway. Contributing to independent wikis is a much better use of your time. https://getindie.wiki/
It’s not Fandom
Might be a minimum of 16 chars. Or the parsing is broken and treats the ’ as the end of the password
Yeah, I’d consider anything less than 20 characters broken. Much too likely that it’s contained in a rainbow table, regardless how many special characters you use. Can I remember many 20 character passwords? No, but my password manager can.
That’s a big rainbow table. Like, with just precomputed values and random ascii character passwords it’s on the order of 1042 entries. You can shave that down a bit probably with all the tricks rainbow tables use, but I think you’re safe.
Base85 contains just about every printable ASCII character, so I’ll use that as a base. 8516 ~= 1031 -> extremely huge, but still feasible at least for state actors. 8520 ~= 1039 -> if I read Wolfram Alpha’s comparison correctly, that is more information than is believed to be contained in the DNA of all living creatures combined. That’s why I’d recommend >= 20 characters.
State actors don’t generally need to break passwords. They ask the company “nicely” and they get what they want. The exception would be if that password is being used to encrypt data.
I let my password manager create 32 char passwords, that should be enough for a while. But of course then you have websites that throw you a ‘your password is too long’ message and have you find out by trial and error that they only accept 12 characters.
Or the off-by-one errors where they insist that 24 chars are the max, but in reality they accept 23. Probably never tested the limit.
Or websites that truncate your password after X characters when registering, but not when logging in, so you end up with an incorrect password and good luck finding out which limit the registration page actually uses.
recently did one that only cared about being very long, so i typed thispasswordisfuckinglong and it took it
Some months back, there was a thread here on Lemmy where people were discussing western names written using Chinese characters. Phonetically, the names will sound alike. But meaning-wise, the characters will result in a Correct Horse Battery Staple-esque string of words.
Which is why I have since decided to make passwords by typing random names into a Chinese name generator and using the English translated result.
Sounds like a lot of work, but the way I see it, trying to think of new passwords is always work so I might as well have fun with it.
Hunter2
I don’t get it, why did you type all asterisks‽
What’s not to get? He made his password 7 asterisks. Funny, because it’s the same as mine.
We are all hunter2 on this blessed day.
“Your selected password is already being used by SwiftyFan05. Please choose another password.”









